Pagers – the new national security threat!
How pagers threaten our security on a daily basis
Unencrypted pagers are still being used by hospitals and industrial environment to send critical and sensitive information. According to The Daily Caller this information could potentially fall into the hands of hackers who hold the data for ransom which could impact budgets or in some cases even national security. Pagers are the riskiest way to send information. Updated secure solutions need to be implemented.
Unencrypted pagers
The decline in pager usage has hit the pager industry hard. The pager industry’s revenue fell from $6.2 billion in 2003 to $2.1 billion in 2008. This lack of interest in the pager has meant that no real improvements have been made to improve functionality and message security. Pagers rarely use encryption, leaving messages sent over the airways unprotected. Using software-defined radio (SDR) and an inexpensive USB dongle, unencrypted messages can be decoded easily.
A recent study did an analysis of the distribution of data types sent via pagers. The results are mapped out in the pie chart below.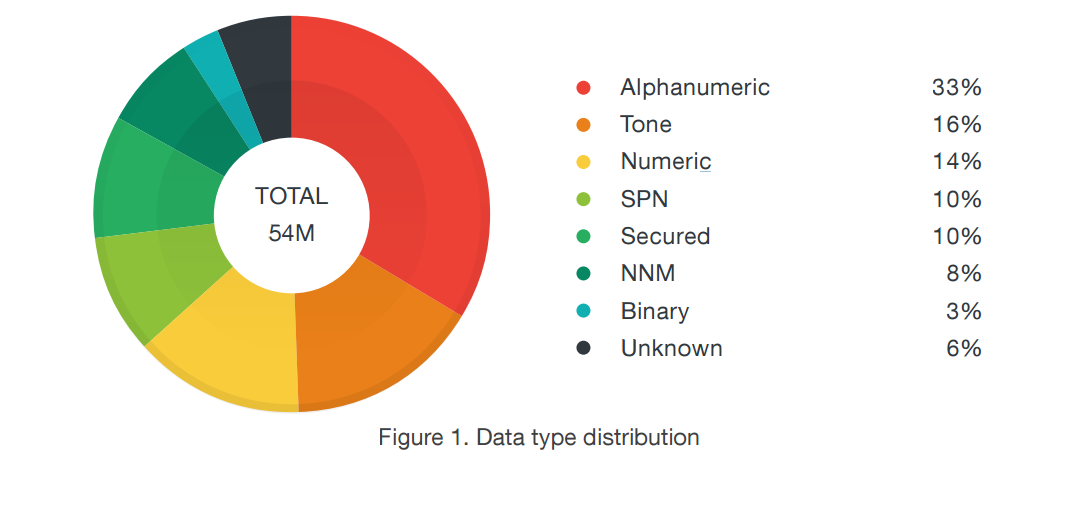 The study which spanned 4 months monitored 54,976,553 records of pages. They found out that 18,368,210 (33%) are alphanumeric and only 10% of the data was actually secured. This data distribution tells us that a lot of information can be gained from pagers which can be collected over time by hackers who specialize in collecting passive intelligence.
The study which spanned 4 months monitored 54,976,553 records of pages. They found out that 18,368,210 (33%) are alphanumeric and only 10% of the data was actually secured. This data distribution tells us that a lot of information can be gained from pagers which can be collected over time by hackers who specialize in collecting passive intelligence.
Passive Intelligence Defined
Passive Intelligence requires an attacker to make contact with the target’s network. Attackers gather information and perform analyses before carrying out their attack. Pages are a really good source of high quality passive intelligence. During the study, pages that were decoded contained information on items such as contact persons, locations inside manufacturers and electricity plants, possible unreported restricted events, intranet IP address, intranet hostnames.
The head of the United Nations nuclear watchdog told reporters earlier this month that this mode of intelligence collection was used in a cyber-attack on a nuclear power plant to smuggle out material that could have allowed terrorists to build a nuclear “dirty bomb.” The director of the International Atomic Energy Agency (IAEA) said that an unidentified individual tried to smuggle a small amount of highly enriched uranium which could have been used to build a so-called “dirty bomb.”
The problem with pagers
The problem with pagers is also seen in their lack of security and reliability when it comes to delivering a page. OnPage’s secure messaging and critical alerting system doesn’t have this problem. A study done by Emory Libraries & Information Technology showcases the following:
Security Issues: Presents potential risk of exposing sensitive information to undesirables.
• No encryption
• No remote wipe capabilities
OnPage facilities are SAS 70 certified and practice SSAE 16 compliance so all our controls and safeguards are in place to secure our client data and to maintain high levels of facility operation through regular auditing. All messages are fully encrypted and remote wipe is a feature of the system.
Reliability issues: Presents risks to patient care
• No message retry (If page is missed, it is lost forever)
• Lack of coverage in low lying areas and basements
• Pager device related issues
• Aging infrastructure
OnPage’s back-end technology includes redundant systems that provide an uninterrupted power supply through battery backups. Multiple emergency backup generators are also on hand and automatically kick-in to further guarantee no power outage. So pages are NEVER lost! Furthermore our Infrastructure is constantly updated along with our application.
Users report missing pages on pagers 97% more often than they report missing pages on cell phones and smart phones. See graph below:
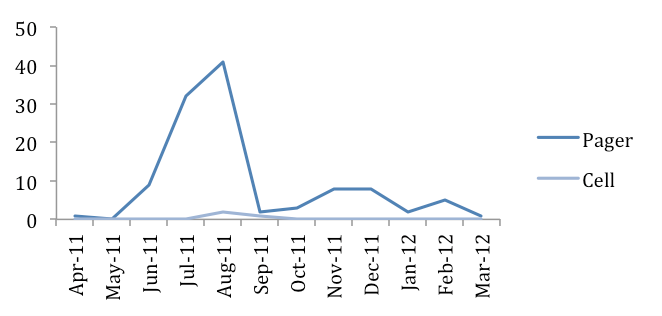
GRAPH 2: No. of pages missed using Pager and Cell
Limited feature set
• One-way messaging only – no rich messaging capabilities, no reply backs.
• Ambiguous – Users, in many cases, cannot see who sent a page to them, which presents risk, especially in the case of no message sent, but only a callback number where there is no answer.
• Text-based messaging only.
OnPage’s messaging and alerting application comes with attachments so you can send an alert and attach sensitive information and rest assured they will be encrypted. With our Audit Trail, you can see when the message is delivered, seen and read.
Lack of closed-loop auditing: Presents risk in malpractice litigation cases
• No delivery acknowledgment or read receipts
• No way to automate escalation of messages
Onpage’s Enterprise web console lets you track a message with delivery acknowledgment or read receipts. Our scheduler can automate escalations to a single person or even groups
Inconsistent with demand
• Many users prefer to consolidate messages (emails, text messages, pages, etc) on one device
• Many users prefer smart device platforms over pagers
• A recent survey at Emory (graph 3: pictured below) showed that approximately 70% of users prefer pages on a cell phone / smart device, while only approximately 15% preferred pagers (remaining 15% chose other options).
OnPage lets you eliminate the need for more than one device and give you complete control over all your critical alerts from one easy to install and use application.
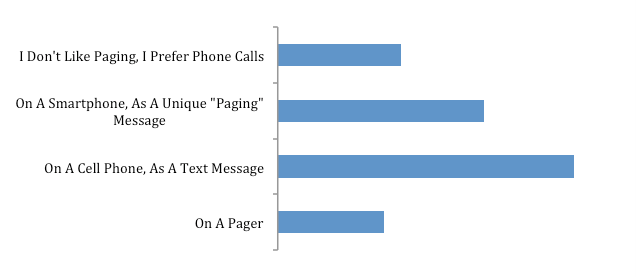
GRAPH 3: Study participant presences
Conclusion
The impacts of using unencrypted pagers are real and dire. They are insecure devices that need to be replaced by healthcare, IT or any industry that relies on them. Failure to do so will leave companies exposed and open to hackers and worse.
To discover more on unencrypted pagers, read our blog on Why Pagers Suck.




