The Importance of Log Monitoring for Incident Response
In the face of growing security threats and incidents, businesses must prioritize their ability to detect, investigate, and respond effectively. Timely incident response is crucial for maintaining the security and integrity of systems and data.
Among the essential tools in the incident response arsenal, log monitoring stands out as a critical component. By closely analyzing logs, organizations gain valuable insights into system events, user activities, and network traffic.
In this article, we will explore the importance of log monitoring for incident response, highlighting its benefits and how it enhances overall security readiness.
What is Log Monitoring?
Log monitoring is the process of continuously analyzing log files generated by systems, applications, and devices. It involves collecting, storing, and analyzing logs in real-time to gain visibility into the IT environment.
By monitoring logs, organizations can detect anomalies, identify security incidents, troubleshoot issues, and ensure system performance. It plays a critical role in incident response by providing insights into the root causes of incidents and facilitating effective remediation.
Log monitoring enhances threat detection, incident response capabilities, and overall system integrity. Log monitoring software like Datadog or its alternatives has become an essential tool in the contemporary development landscape, enabling effective log monitoring practices.
Log Monitoring and Incident Response
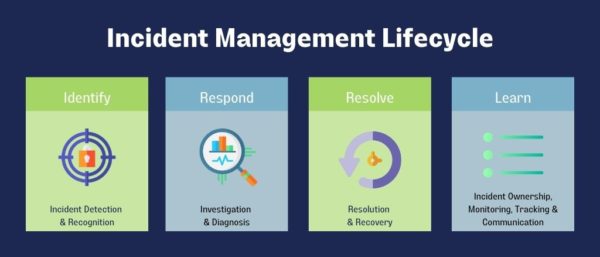
Log monitoring is essential for incident response as it enables organizations to detect and analyze security incidents, system failures, and operational issues. By monitoring log files, organizations can:
- Identify patterns and anomalies
- Receive real-time alerts
- Investigate potential threats promptly
Log monitoring also aids in incident analysis, root cause identification, and implementing necessary remediation measures.
It Helps Identify Incident Indicators
Logs are valuable sources of information for identifying incident indicators. By analyzing log data, organizations can:
- Gain insights into events and activities occurring within their systems, networks, and applications.
- Reveal details such as user access, actions performed, network connections, and system performance metrics.
- Identify suspicious or abnormal behavior that may indicate a security incident.
- Identify unauthorized access attempts, unusual data transfers, or patterns of activity that deviate from normal usage.
It Helps Analyze Root Cause of an Incident
Logs play a crucial role in analyzing the root causes of security incidents. By examining log data before, during, and after an incident, organizations can uncover the factors or vulnerabilities that contributed to its occurrence.
Logs provide insights into the state of systems, user actions, security tool alerts, and incident response activities. Analyzing logs can help determine if:
- Systems were properly patched and updated
- Security best practices were followed
- Any malicious activity was detected or blocked
By reviewing and comparing logs, organizations can identify gaps, inconsistencies and find out how the incident happened and what could be done to mitigate it. This analysis enables organizations to strengthen their security measures, address underlying issues, and reduce the risk of future incidents.
Try OnPage for FREE! Request an enterprise free trial.
How to Improve Your Logging Capabilities and Policies?
To enhance logging capabilities and policies, organizations should start by defining clear objectives and requirements for their logs. This includes identifying the types of logs needed, the duration of log retention, and how they will be utilized for incident handling.
Systems, networks, and applications should be properly configured to generate accurate and comprehensive logs that align with these objectives. It’s important to establish a log retention policy that outlines storage, protection, and disposal procedures.
Regular review and auditing of logs ensure their completeness, reliability, and security, further improving an organization’s incident-handling capabilities and overall security posture.
Log Monitoring Benefits for Incident Response Strategy
By analyzing logs, organizations can detect anomalies, suspicious patterns, and indicators of compromise, enabling them to take proactive measures to mitigate risks and protect their systems and data. This proactive approach is beneficial for many reasons, such as:
1. Increasing the speed of issue recognition by alerting

By leveraging log monitoring and alert management tools, organizations can enhance incident response and maximize investments in log monitoring tools.
The integration allows organizations to automate alert delivery to the appropriate on-call staff when specific events are triggered, enabling swift identification and response to potential issues or security incidents. Alerts are automated based on pre-defined routing policies and on-call schedules.
This proactive approach helps minimize the impact of incidents and facilitates faster resolution, ultimately improving the overall incident response capabilities of the organization.
The Incident Response Strategy also plays a crucial role in AWS monitoring. It involves continuously analyzing and monitoring logs generated by various AWS services and enables early detection, real-time alerting, investigation and forensics.
This can bolster their security capabilities and effectively respond to security incidents in their AWS environment.
2. Timely analysis of possible application or system issues
Log monitoring enables organizations to quickly identify and analyze possible application or system issues.
By monitoring logs in real-time, organizations can proactively detect errors, anomalies, or performance degradation, allowing them to address these issues promptly and minimize their impact on business operations.
3. Customization of the traditional path
Log monitoring offers the flexibility to customize the traditional incident response path. Organizations can tailor their log monitoring strategies to align with their specific needs, priorities, and regulatory requirements.
This customization empowers organizations to respond effectively to incidents based on their unique circumstances, enhancing the efficiency and effectiveness of their incident response efforts.
4. Automatic log monitoring and IT ticketing
Integrating log monitoring with IT ticketing systems streamlines the incident response process. Automatic log monitoring tools can generate and assign IT tickets based on predefined rules or triggers identified in the logs. IT tickets can in turn be integrated into alerting tools to elevate critical P1 tickets.
This automation reduces manual effort, improves response times, and ensures that incidents are properly tracked, prioritized, and resolved.
5. Simplify analysis with log monitoring
Log monitoring simplifies the analysis of system behavior and security events.
By aggregating and correlating logs from multiple sources, organizations gain a comprehensive view of their IT environment. This holistic perspective enables easier detection of patterns, anomalies, and potential security threats.
Try OnPage for FREE! Request an enterprise free trial.
Types of Logs That Are Crucial for Incident Detection
Incident detection relies on various types of logs that provide valuable insights into different areas of an organization’s IT infrastructure. Here are some key types of logs that play a crucial role in incident detection:
- Windows event logs: Windows operating systems generate event logs that capture information about user activities, system events, and security-related incidents.
- Perimeter device logs: Logs generated by network perimeter devices such as firewalls, routers, and intrusion detection systems (IDS) help monitor network traffic, identify potential threats, and detect unauthorized access attempts.
- Endpoint logs: Logs from endpoints, including workstations and servers, offer insights into user activities, application usage, system performance, and security-related events.
- Application logs: Applications generate logs that capture information about their operations, errors, and user interactions.
- Proxy logs: Proxy servers record logs of web traffic, including URLs accessed, IP addresses, and user activities.
- IoT logs: Internet of Things (IoT) devices generate logs that capture device activities, sensor readings, and connectivity events.
Use Cases of Log Monitoring

Log monitoring enables organizations to effectively detect, investigate, and respond to security incidents. Here are two key use cases that highlight the importance of log monitoring in incident response.
1. Detecting and Mitigating a Data Breach
Log monitoring can help identify indicators of a potential data breach by analyzing various logs, such as network traffic logs, authentication logs, and application logs.
By monitoring for suspicious activities, unusual patterns, or unauthorized access attempts, organizations can detect and respond to data breaches promptly.
2. Identifying and Resolving System Vulnerabilities
Log monitoring allows organizations to proactively identify system vulnerabilities and potential exploits. By analyzing logs from various sources, including endpoint logs, application logs, and system logs, organizations can detect anomalies, errors, or configuration issues that could be exploited by attackers.
Timely identification of such vulnerabilities enables organizations to take remedial actions to mitigate the risk of an incident.
In Conclusion
Log monitoring plays a crucial role in incident response strategies. By actively monitoring and analyzing various logs, organizations can effectively detect and respond to security incidents.
The benefits of monitoring logs include quick incident recognition through alerts and integration with alert management tools. It enables root cause analysis, improves logging capabilities and policies, and simplifies incident analysis.
Log monitoring supports use cases such as data breach detection, vulnerability identification, and proactive risk mitigation.
In today’s dynamic digital landscape, investing in log monitoring tools, processes, and skilled personnel is essential for organizations to protect their data, systems, and reputation. It enhances incident response capabilities and effectively mitigates security incidents.







