Top 7 SOAR Tools (as of 2026)

Security Orchestration, Automation, and Response (SOAR) platforms empower security teams to streamline and accelerate their response to cyber threats. By integrating with existing security tools, automating repetitive tasks, and standardizing incident response workflows, SOAR helps organizations proactively defend against attacks while improving operational efficiency.
Security teams are often overwhelmed by manual processes and alert fatigue, so SOAR solutions offer a smarter, faster way to manage incidents by reducing costs, closing coverage gaps, and boosting overall productivity.
SOAR tools work in tandem with alerting tools to ensure that in the case of severe cyber incidents teams can act fast, no matter when or where.
In this blog, I’ll explore the top SOAR tools available today and how they can enhance your cybersecurity measures.
What does SOAR stand for?
SOAR stands for Security Orchestration, Automation, and Response. Let’s dive deeper into what each letter stands for:
Security Orchestration – The process of connecting and coordinating various security tools and systems to streamline operations. It ensures that data and actions flow efficiently between technologies, creating a more unified security ecosystem.
Automation – The execution of tasks – like alert triage, enrichment, or containment – without human intervention, using predefined rules and workflows to reduce response times and analyst workload.
Response – The actions taken to investigate, contain, and remediate security incidents. This includes both automated and analyst-driven efforts to minimize damage and restore normal operations.
What’s the difference between SOAR vs. SIEM?
Many people conflate the two acronyms SIEM and SOAR, so I want to share the differences, while highlighting how they complement each other. Security Information and Event Management (SIEM) tools collect, aggregate and analyze security data like logs and alerts across an organization’s systems where SOAR automates and coordinates the response to the threats detected by these SIEM tools (or other forms of threat detection).
After identifying the key differences is it important to note how SIEM and SOAR go hand-in-hand. SIEM tools will detect and prioritize potential threats, and when integrated with SOAR solutions deliver critical alerts. Then SOAR handles the rest by automatically responding to critical issues by gathering context, assigning tasks or even automating solutions based on predefined playbooks.
So, with a better understanding of SOAR and how it is used, I want to take a look at the key benefits of implementing SOAR solutions.
Key Benefits of SOAR Solutions
Faster Incident Response – With automation capabilities and predefined playbooks, teams can reduce mean time to detect and mean time to respond (MTTR). Additionally, during more critical incidents that require manual intervention, SOAR systems integrate with your alerting tools to ensure that security teams are mobilized immediately.
Improved Efficiency – By automating manual, low-value tasks, security analysts can free up their time to focus on complex investigations.
Consistent Workflows – SOAR solutions help to standardize incident response procedures, while ensuring uniform processes and little to no human error.
Better Threat Visibility – These systems centralize data from multiple security tools into a single platform, making threat detection and investigation easier.
Reduced Alert Fatigue – Teams can correlate and prioritize alerts from various sources, filtering our false positives and helping analysts focus on real threats. Alerting can be significantly enhanced with the use of incident management solutions that deliver loud, distinguishable push notifications that bypass Do Not Disturb on mobile devices.
7 Best SOAR Solutions
Google Security Operations
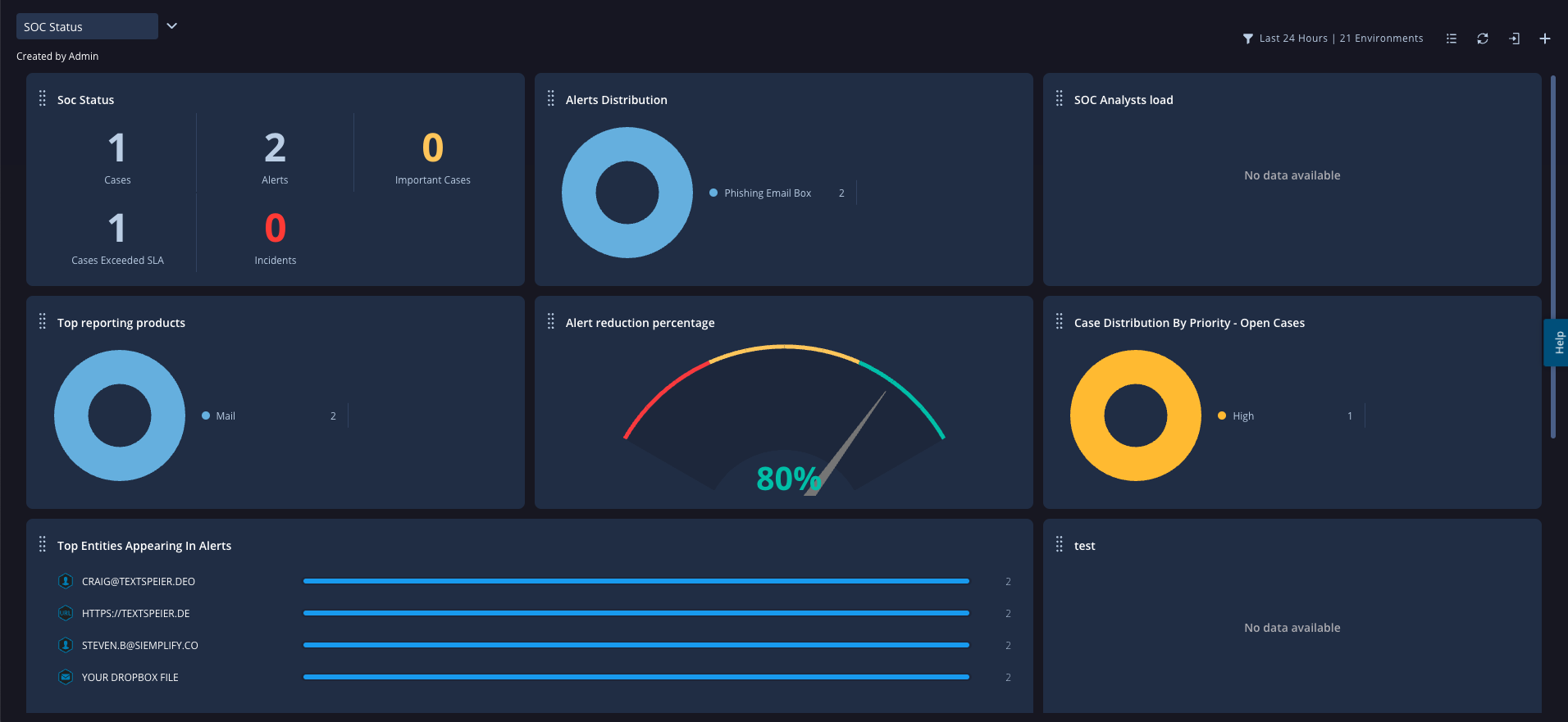
Google Security Operations delivers advanced SOAR capabilities through a unified platform that combines threat detection, investigation, and response. Built on Google Cloud’s secure infrastructure, it offers powerful threat intel enrichment, case management, and automation playbooks. With tight integrations into Google’s ecosystem and Mandiant threat intelligence, this SOAR tool empowers SOC teams to reduce MTTR and improve security outcomes.
Ratings
G2: 4.5/5
TrustRadius: 7.8/10
IBM Security QRadar
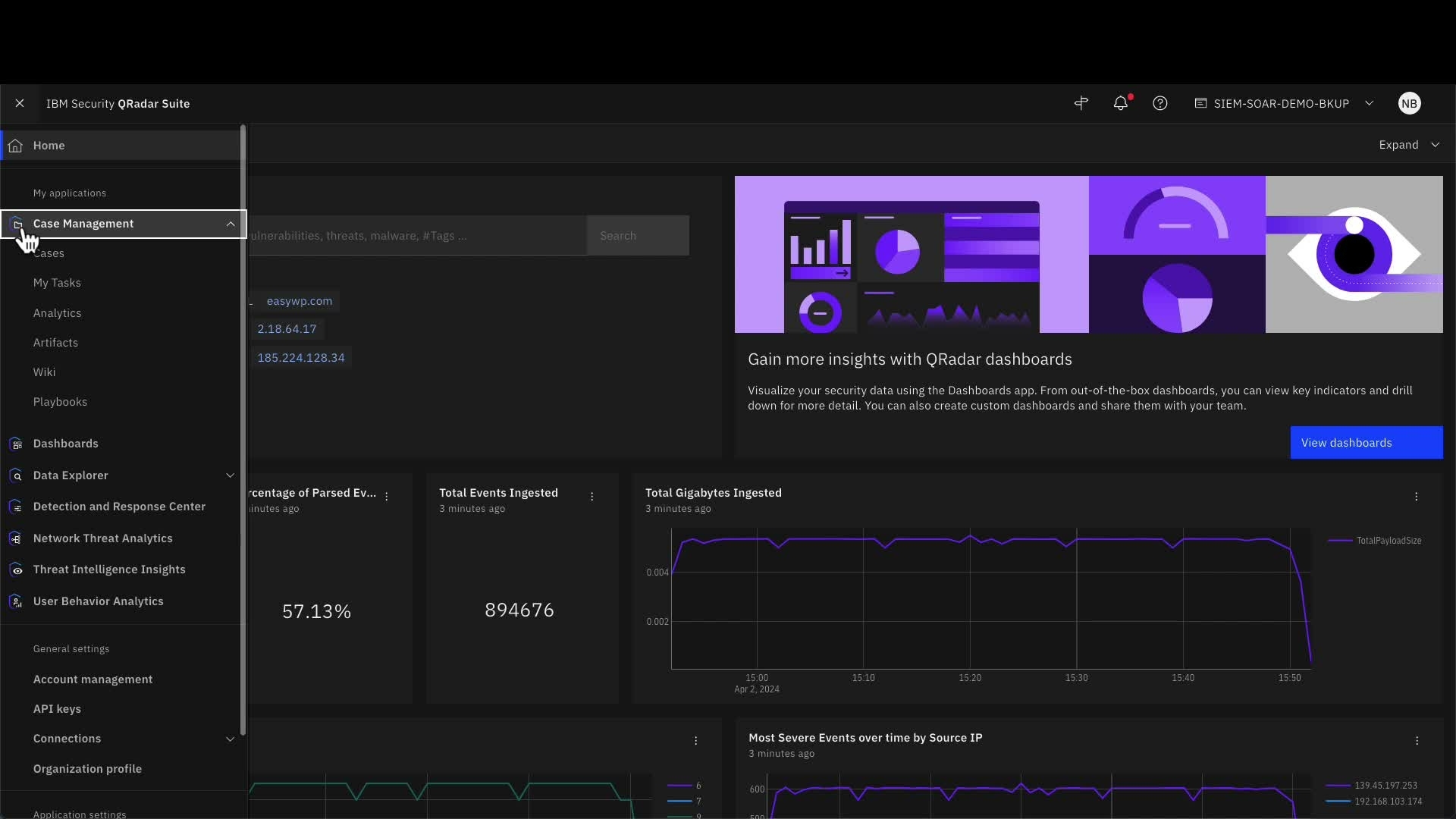
IBM Security QRadar is designed to help security teams respond to incidents with speed and precision. It features dynamic playbooks, case management, and integration with QRadar SIEM for unified threat detection and response. QRadar SOAR supports the NIST Cybersecurity Framework and enables customizable workflows to meet compliance needs and incident response procedures at scale.
Rating
G2: 4/5
TrustRadius: 8.6/10
Microsoft Sentinel
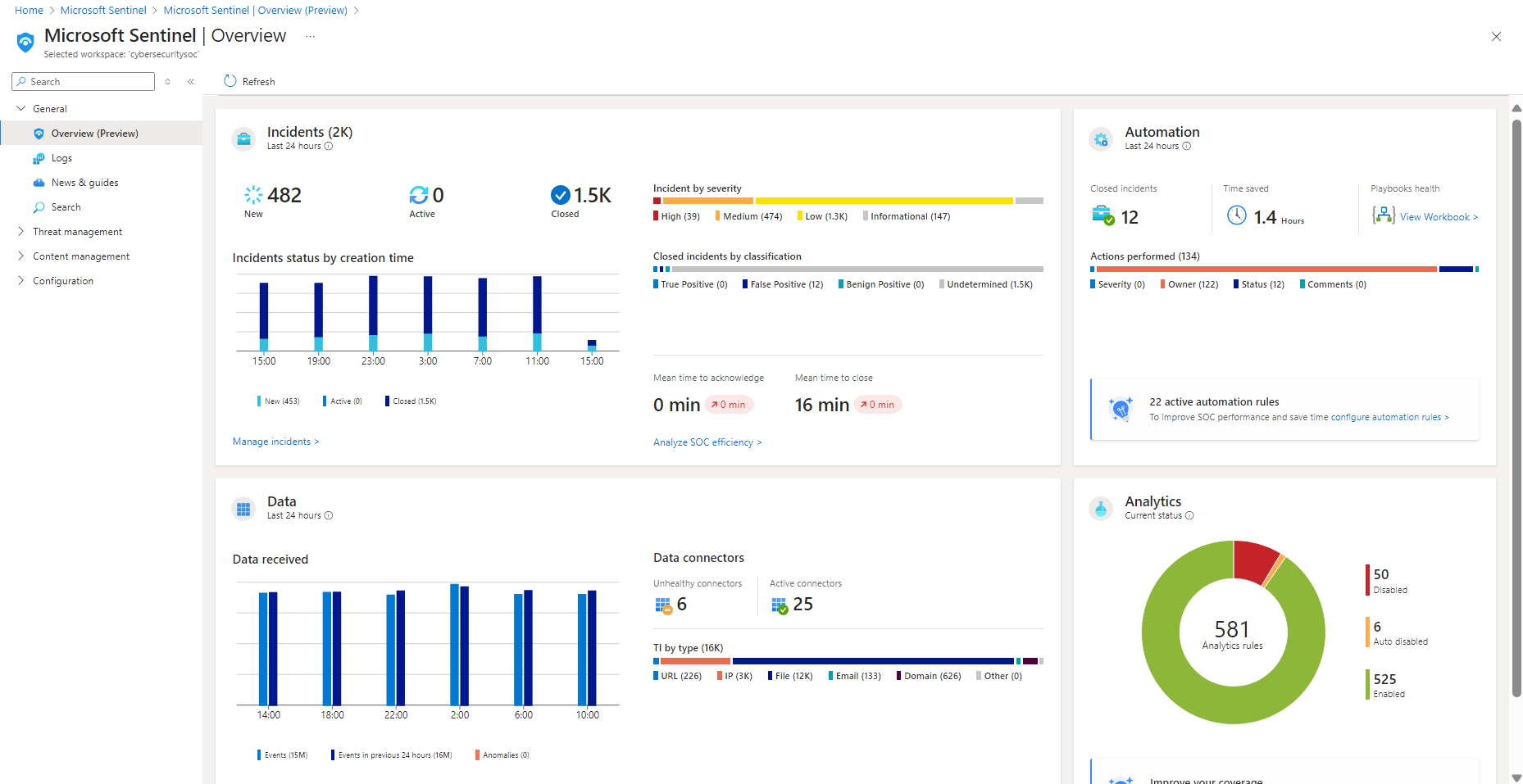
Microsoft Sentinel is a cloud-native SIEM and SOAR solution that integrates seamlessly with Microsoft 365, Azure, and third-party security tools. With built-in automation and orchestration capabilities via Logic Apps, Sentinel empowers security teams to detect, investigate, and respond to threats efficiently. Its AI-driven insights, threat intelligence, and extensive automation support make it a scalable solution for modern cloud-first organizations.
Rating
G2: 4.4/5
TrustRadius: 8.4/10
ServiceNow Security Operations
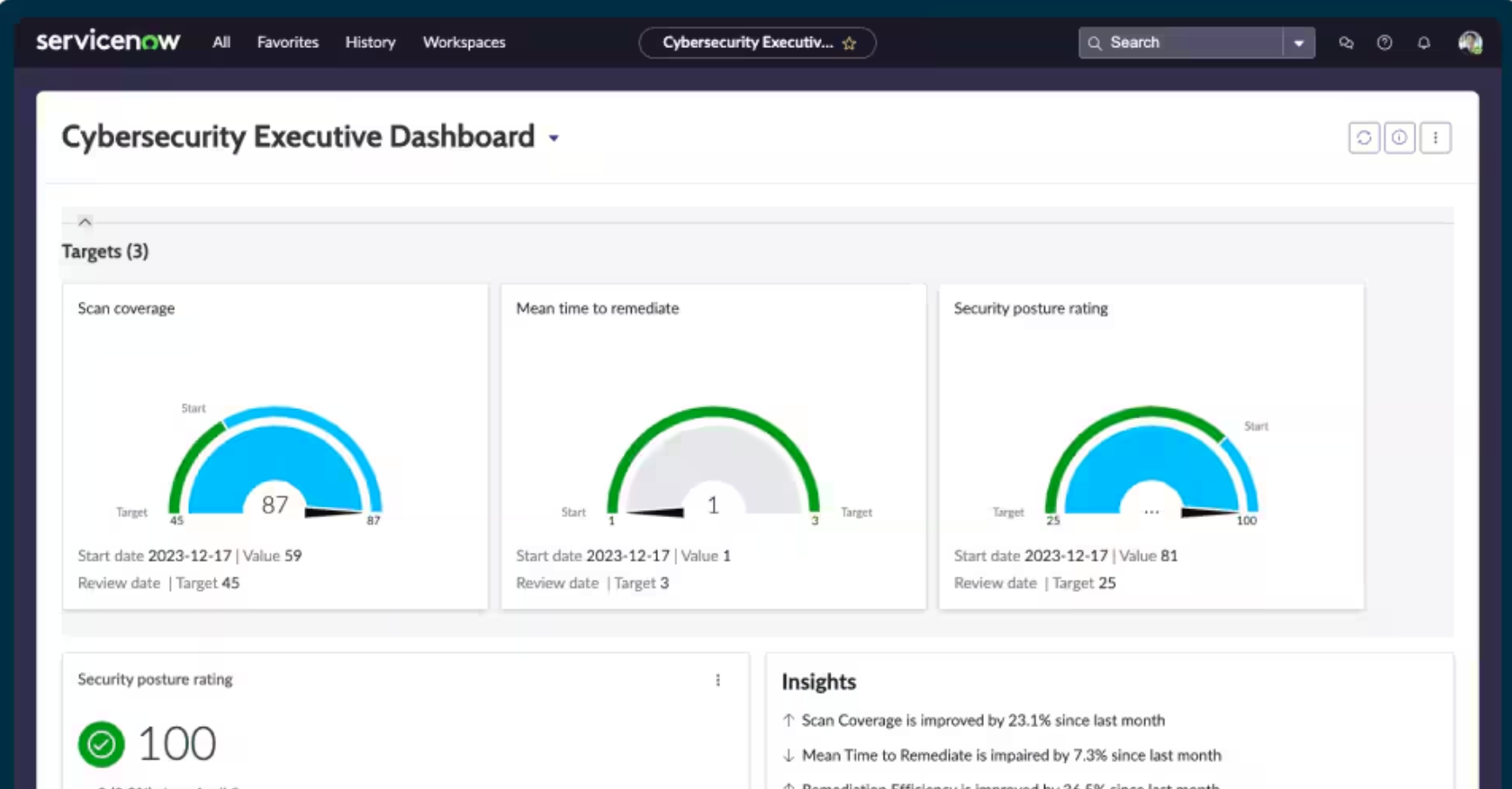
ServiceNow Security Operations bridges IT and security with workflow-driven incident response, vulnerability management, and threat intelligence enrichment. Built on the Now Platform, it enables efficient collaboration between security and IT teams. Automation, case correlation, and threat intelligence integrations streamline the investigation process and help reduce response time significantly.
Ratings
G2: 4.5/5
TrustRadius: 10/10
Splunk SOAR
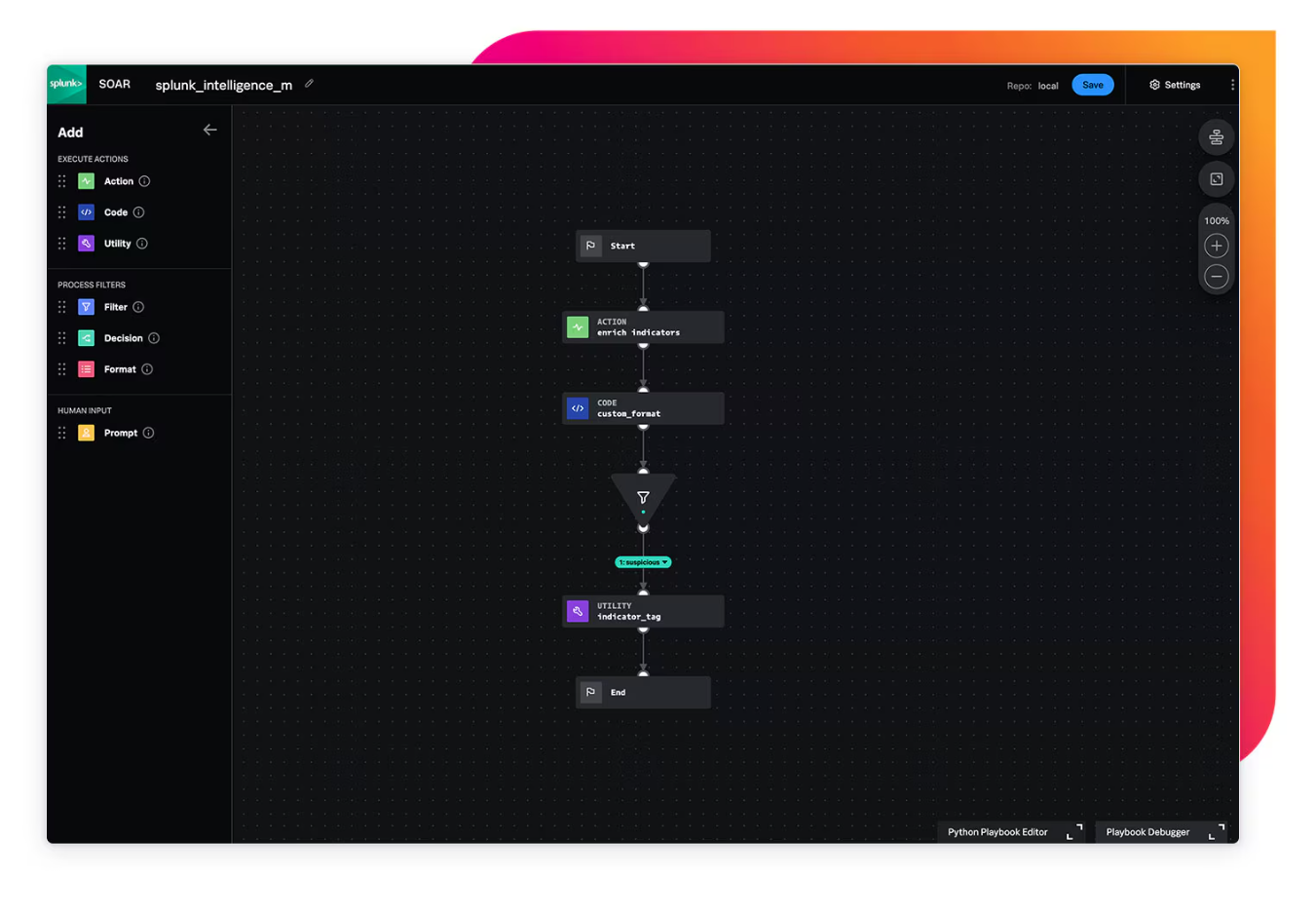
Splunk SOAR allows security teams to automate repetitive tasks, orchestrate complex workflows, and respond to incidents at machine speed. Integrated with Splunk’s analytics-driven SIEM, it offers over 300 pre-built integrations and a visual playbook editor for fast deployment. Its powerful automation engine helps SOC teams save time, improve consistency, and scale their operations with confidence.
Ratings
G2: 4.4/5
TrustRadius: 8.4/10
Sumo Logic Cloud SOAR
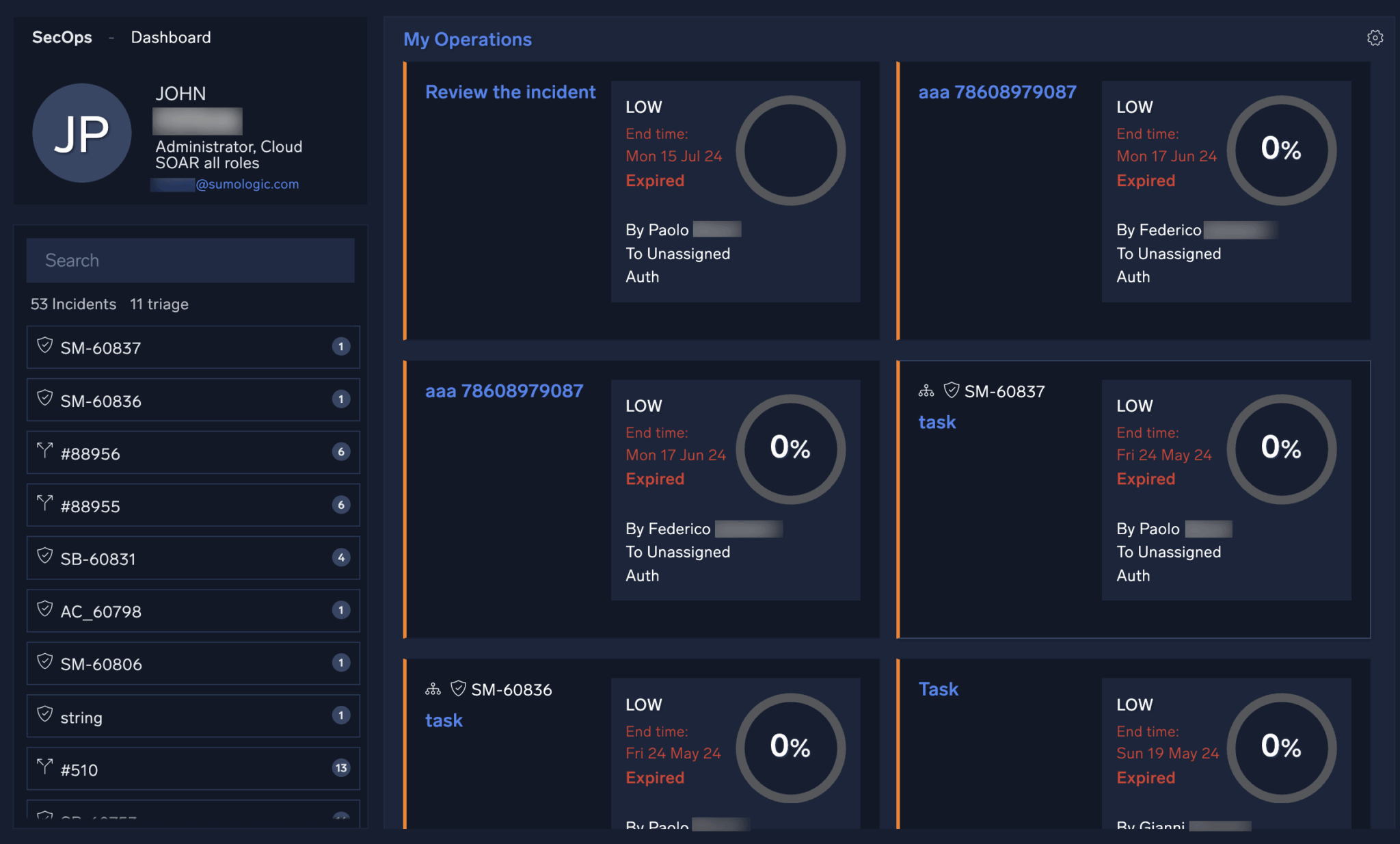
Sumo Logic Cloud SOAR is a modern, cloud-native SOAR platform that emphasizes intuitive playbook creation, dynamic case management, and seamless integration with threat intelligence sources. Designed for MSSPs and enterprise SOCs, it supports multi-tenant environments and collaborative incident response. Its flexibility and cloud-native foundation make it a strong fit for agile security operations.
Ratings
G2: 4.3/5
TrustRadius: 8.9/10
Tines
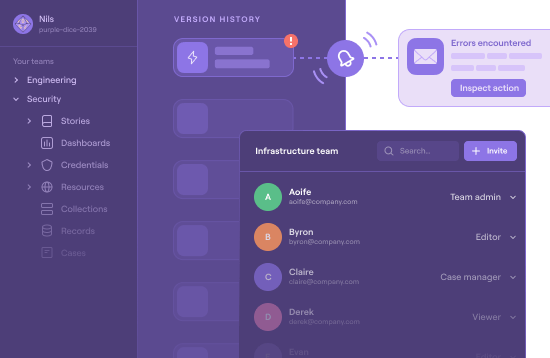
Tines is a no-code automation platform tailored for security teams. It stands out with its easy-to-use interface, allowing users to build and run sophisticated automation stories without writing code. Tines supports hundreds of integrations, and excels in use cases like phishing response, alert triage, and user provisioning. It’s particularly popular with modern SOCs looking for flexibility and speed in their response workflows.
Ratings
G2: 4.5/5
SOAR and OnPage
In the end, no matter which SOAR tool your team employs, integrating it with an effective incident alerting is imperative. These solutions are tasked with notifying teams for various reasons including, escalations of high-severity threats, missed SLAs, critical system changes, or when manual intervention is required to contain or remediate an incident. Natively SOAR systems rely on emails and in-app notifications to notify team members of critical situations, which are incredibly ineffective if the responders are not constantly monitoring their email or SOAR dashboard. So, many SOCs integrate with OnPage to deliver push notifications to their on-call security analysts, allowing them to benefit from features like:
Digital On-Call Scheduling – Teams can create digital on-call schedules that ensure alerts are being sent to the security analyst who is on-shift at that time. This reduces manual error and eliminates the use of paper, manual schedules.
Automated Escalations – In the unlikely case that the primary analyst is unable to respond, OnPage automatically escalates the alert to the next person on-call to ensure that no alert is left unresolved and SLAs are always met.
High Priority Alerting – OnPage high priority alerts are loud, distinguishable and even bypass the silent switch, unlike emails that often slip through the cracks and don’t effectively mobilize security staff.
Conclusion
Choosing the right SOAR platform is a critical step in modernizing your security operations. Whether your team prioritizes deep integrations, no-code automation, or built-in threat intelligence, each of the solutions listed, Google Security Operations, IBM QRadar SOAR, Microsoft Sentinel, ServiceNow Security Operations, Splunk SOAR, Sumo Logic Cloud SOAR, and Tines, brings unique strengths to the table.
Regardless of the tool you choose, one thing remains consistent, a SOAR platform is only as effective as its ability to notify the right people at the right time. Integrating your SOAR with a reliable incident alerting solution ensures that critical threats don’t go unnoticed, enabling your team to respond swiftly and confidently.






